A basic Spring Web Flux App
Let's start by creating a simple Spring Boot application using the Spring Initializr:
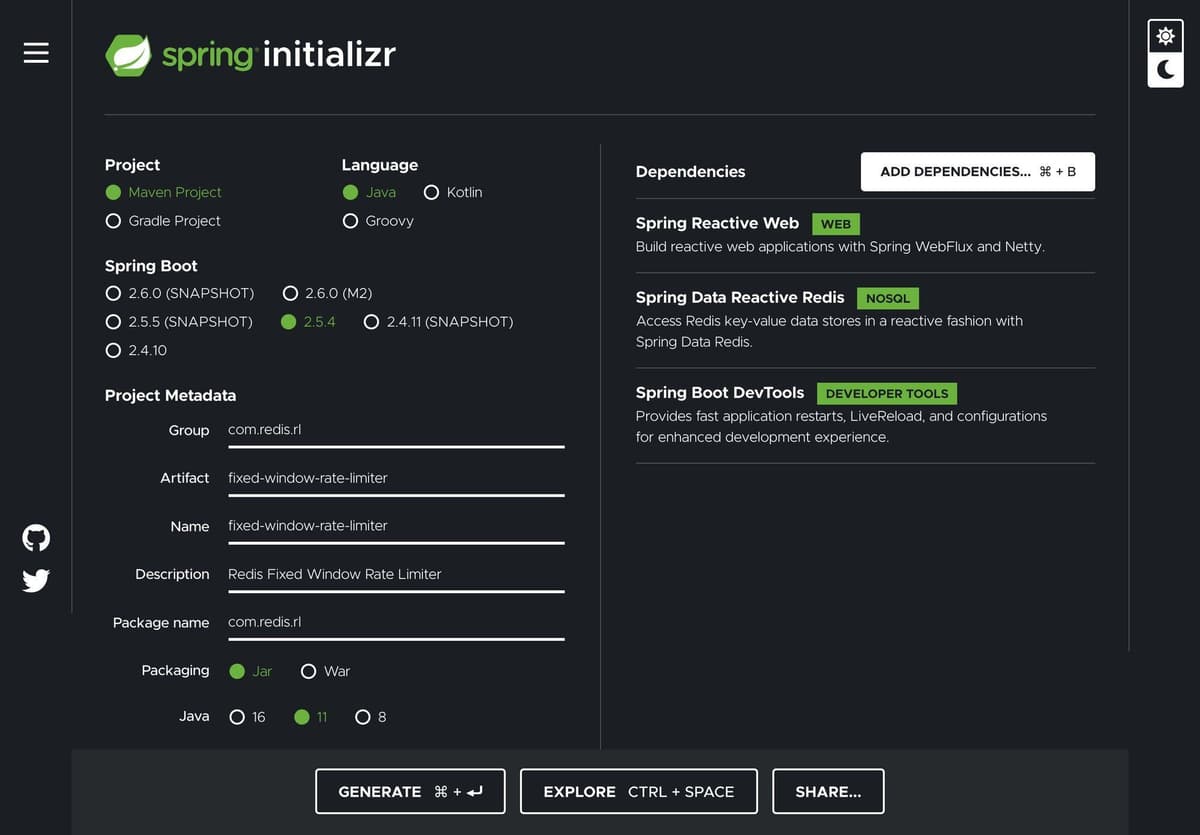
- In your browser, launch the Spring Initilizr
- Fill out the form using the following settings:
- Project: Maven Project
- Language: Java
- Spring Boot: 2.5.4
- Project Metadata:
- Group:
com.redis.rl - Artifact:
fixed-window-rate-limiter - Name:
fixed-window-rate-limiter - Description: Redis Fixed Window Rate Limiter
- Package Name:
com.redis.rl - Packaging: JAR
- Java: 11
- Group:
- Dependencies:
- Spring Reactive Web
- String Data Reactive
- Spring Boot DevTools
Click on GENERATE and Initializr will generate the zip file for the project and prompt you to download it to your local machine. Unzip the downloaded file (named fixed-window-rate-limiter.zip) in a suitable directory. For example on a Mac:
Now, open the file FixedWindowRateLimiterApplication.java located under fixed-window-rate-limiter/src/main/java/com/redis/rl/:
And let's add the @Bean annotated method routes() to create the simplest of endpoints; a "ping" endpoint, which replies with a text reponse "PONG":
You'll also need the following imports:
Let's use curl to test the newly created endpoint:
Spring WebFlux Filters
We'll implement our rate limiter as a Spring WebFlux Filter. A filter allows us to intercept a request and modify the response. For our needs we'll use a HandlerFilterFunction; which we can filter a RouterFunction such as our routes() endpoint.
We'll keep everything in one file to make the example easier to manage for our simple example. At the end of the file FixedWindowRateLimiterApplication.java let's add a class called RateLimiterHandlerFilterFunction as shown:
The class implements the filter method, which currently returns null. Let's modify it to simply pass the request throught.
And also, let's apply it to our routes method:
Testing the endpoint with curl should still works as previously.
Reactive Redis Template
Spring Data Redis provides a Reactive API which plays well with all the other reactive parts of the Spring framework. In order to work with Redis we'll use the ReactiveRedisTemplate, the aptly named reactiveRedisTemplate method configures a reactive template given a ReactiveRedisConnectionFactory (which will be injected by the framework).
The template is configured to use the work with String keys and Long values as shown by the usage of the StringRedisSerializer and the GenericToStringSerializer.
The template offers a high-level abstraction for Redis interactions and we will later pass it to our rate limiter filter to use Redis as our rate limiting back-end:
Below are the required imports added:
Next, let's modify the RateLimiterHandlerFilterFunction class to include the template and let's add a constructor so that we can properly initialize it:
We also need to modify the routes method to include the redisTemplate in the call to the RateLimiterHandlerFilterFunction constructor:
Identifying the Requester
As mentioned in the introduction to rate limiting, identifying the origin of the request is critical to the efficacy of your rate limiting implementation. In this simple implementation we will focus on the mechanics of rate limiting and do the simplest possible thing we can do to identify the requester.
The filter method in RateLimiterHandlerFilterFunction takes an instance of a ServerRequest, from which we can obtain the IP address of the requester. Add private method requestAddress to the filter function class:
With the requestAddress in place we can build the key we'll use to check for the requesters' quota. To compute the key we will concatenate the requester's address and the current minute of the hour. We'll prefix the keys with rl_ for "rate limiting":
Invoking the endpoint should show the key on the console like:
Increment and Expire Key
Now we need to implement the logic to execute the INCR and an EXPIRE logic outlined in Fixed Window implementation using Spring Data Redis Reactive:
The "Basic Rate Limiting" recipe calls for the use of a Redis Transaction in which the commands are sent to the server, accumulated in serial way and executed sequentially without any possible interruption by a request from another client.
Basically, we want the INCR and EXPIRE calls to update the requests-per-unit-of-time counter to happen atomically or not at all. Given that a Reactive API and Redis Transactions (MULTI/EXEC) are not compatible paradigms, which boils down to "you cannot listen to a command that is going to be executed in the future" in a chain of reactive commands A "best possible" approach to achieve this behavior with a reactive API is by using the ReactiveRedisTemplate execute method which takes a ReactiveRedisCallback guaranteing that at least the commands will run on the same Redis connection, but, this is by no means a real "transaction":
Let's break down what this monster of a reactive method:
- The method returns an Asynchronous (0-1) Result, a
Mono(a specializedPublisher<T>that emits at most one item in this case aServerResponse) - The method takes the calculated rate limiting
key, the original serverrequestandnexthandler function - In the
doInRedismethod we turn the key into aByteBufferin order to use withReactiveRedisConnectioncommands - The zip methods waits for all the sources to emit one element and combines these elements into an output value ,which we are ignoring since all we are after is sequential execution on the
INCRandEXPIREcommands. - The method then returns a
Mono.empty() - Finally handle the request.
Completing the filter implementation
To complete the filter implementation, we'll add a constant for the cap on the number of request per minute, that can be optionally loaded from the application's properties:
Let's break down he final filter method implementation:
- We use the Redis template
opsForValue()to retrieve the value stored under the calculated key. - If the value..
- Is greater than or equal to the max quota we deny the request with a 409 response.
- Otherwise, call
incrementAndExpireKey
-
- Is empty/key not found (first request on this window) we call
incrementAndExpireKey
- Is empty/key not found (first request on this window) we call
Testing with curl
A simple way to test an API rate limiter is using curl in a loop, since we are testing a set number of requests per unit of time the curl loop below will suffice:
We loop 22 times, the example code is set to 20 so 22 will allow us to see two 429 responses. The curl flags used are as follows; first is -s that silences curl (makes it hide progress bar and errors), -w is the write out options in which we can pass a string with interpolated variables. Then we sleep 1/2 second between cycles.
If we run Redis in monitor mode, we should see the call to GET for a rejected request, and the same plus calls to INCR and EXPIRE for an allowed request:
You can find this example on the main branch at https://github.com/redis-developer/fixed-window-rate-limiter
